Kubernetes (or K8s) is inherently complex, making it challenging to grasp and even harder to implement in deployments—especially for developers new to the technology.In addition to that, managing code changes in a Kubernetes cluster can be complex, especially when multiple applications are involved, as keeping track of changes, versions, and dependencies can be challenging, leading to conflicts that may impact cluster stability.
Here comes the Savior, GitOps - which leverages your git commit history to auto create,read,update and delete applications on your k8s cluster. In shorter terms - Making Git as a single source of truth. All you have to do is to make a commit in your Code Hosting platforms like Github, GitLab and BitBucket and your k8s clusters will ready to deploy with your latest changes!

This article illustrates how to integrate FluxCD to help you streamline your deployments.
What is FluxCD?
Flux is an open source tool to streamline your deployments using Git. Flux is a package management system that operates on a Git-based platform, delivering a range of smooth and incremental deployment solutions for Kubernetes. Its primary objective is to maintain synchronization between Kubernetes clusters and configuration sources such as Git repositories. It achieves this by automating the updating of configurations whenever new code is available for deployment.
Here is the Website - https://fluxcd.io/ and the Github Repo - https://github.com/fluxcd/flux2
Features of FluxCD
• Automated Deployments: Flux CD streamlines deployments by continuously monitoring a Git repository for updates and automatically applying changes to the cluster. This minimizes manual effort, reduces errors, and ensures consistent application rollouts.
• GitOps Workflow: Adhering to the GitOps model, Flux CD allows developers to manage the desired state and configuration changes through Git repositories. This approach enhances version control, fosters collaboration, improves auditability, and simplifies the change management process.
• Progressive Delivery: Through Flagger, Flux CD supports advanced deployment strategies like canary releases, blue/green deployments, and A/B testing. These techniques allow teams to roll out changes safely and gradually, reducing risk and ensuring production stability.
• Security by Design: Flux CD emphasizes security through pull-based operations, least privilege access, and smooth integration with security tools. These practices ensure a secure deployment pipeline and protect sensitive resources throughout the process.
• Tooling Compatibility: Flux CD integrates seamlessly with widely-used Kubernetes tools such as Kustomize, Helm, GitHub, GitLab, Harbor, custom webhooks, and policy frameworks like OPA and Kyverno. This flexibility makes it easy to incorporate Flux CD into existing workflows while using preferred tools.
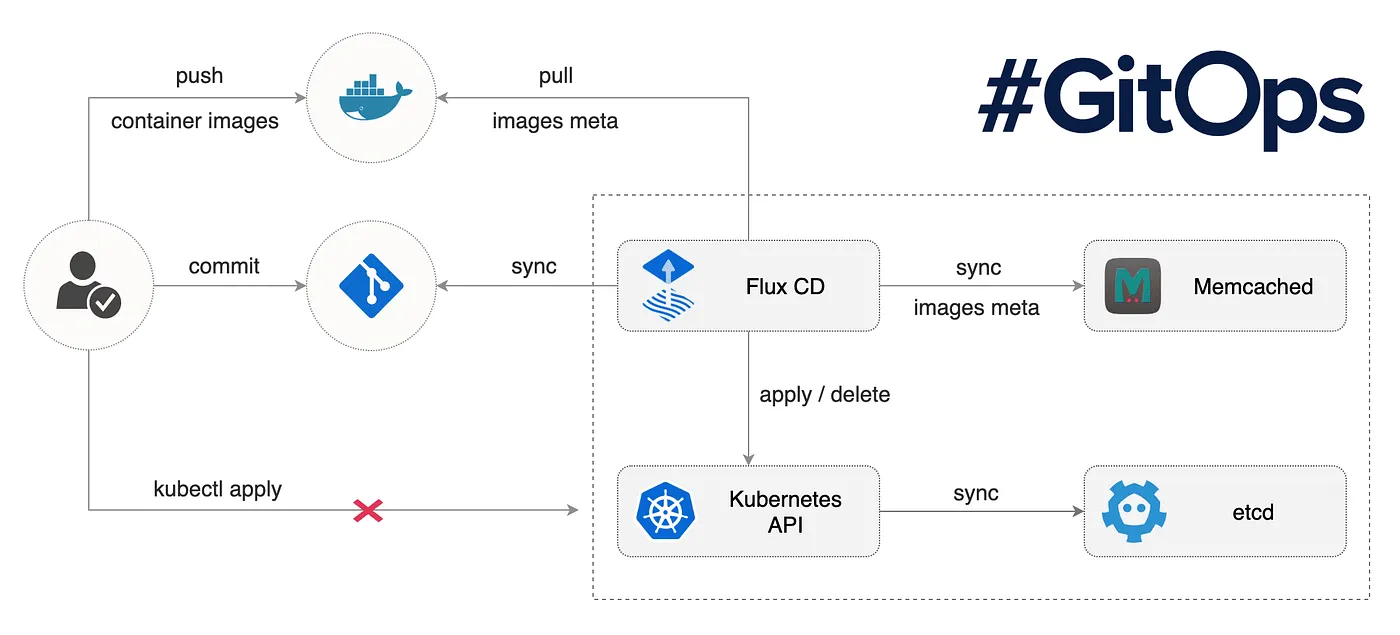
Understanding the FluxCD Controllers
There are 5 types of Flux CD Controllers which from the basis of GitOps operations. Each is designed for a very specific purpose -
Source Controller - The main role of the source management component is to provide a common interface for artifacts acquisition. The source API defines a set of Kubernetes objects that cluster admins and various automated operators can interact with to offload the Git and Helm repositories operations to a dedicated controller.
Features:
Validate source definitions
Authenticate to sources (SSH, user/password, API token)
Detect source changes based on update policies (semver)
Fetch resources on-demand and on-a-schedule
Package the fetched resources into a well-known format (tar.gz, yaml)
Make the artifacts addressable by their source identifier (sha, version, ts)
Notify interested 3rd parties of source changes and availability (status conditions, events, hooks)
Kustomize Controller - The kustomize-controller is a Kubernetes operator, specialized in running continuous delivery pipelines for infrastructure and workloads defined with Kubernetes manifests and assembled with Kustomize.
Features:
Reconciles the cluster state from multiple sources (provided by source-controller)
Generates manifests with Kustomize (from plain Kubernetes YAMLs or Kustomize overlays)
Helm Controller - The Helm Controller is a Kubernetes operator, allowing one to declaratively manage Helm chart releases with Kubernetes manifests.
Helm is a package manager for Kubernetes that allows users to install, update, and roll back applications. Helm charts can be used to describe applications, install them repeatedly, and provide a single point of authority.
Features:
Watches for
HelmReleaseobjects and generatesHelmChartobjectsSupports
HelmChartartifacts produced fromHelmRepositoryandGitRepositorysourcesFetches artifacts produced by source-controller from
HelmChartobjectsWatches
HelmChartobjects for revision changes (including semver ranges for charts fromHelmRepositorysources)Performs automated Helm actions, including Helm tests, rollbacks and uninstalls
Notification Controller - The Notification Controller is a Kubernetes operator, specialized in handling inbound and outbound events. The controller handles events coming from external systems (GitHub, GitLab, Bitbucket, Harbor, Jenkins, etc) and notifies the GitOps toolkit controllers about source changes.
Image Reflection And Updation Controller - The image-reflector-controller and image-automation-controller work together to update a Git repository when new container images are available.
The image-reflector-controller scans image repositories and reflects the image metadata in Kubernetes resources.
The image-automation-controller updates YAML files based on the latest images scanned, and commits the changes to a given Git repository.
Setting up your Flux Configuration
Install Flux CLI -
curl -s https://fluxcd.io/install.sh | sudo bash
Verify Flux pre-check for Kubernetes cluster:
flux check --pre
► checking prerequisites
✔ Kubernetes 1.27.2 >=1.24.0-0
✔ prerequisites checks passed
Flux BootStrap for your Github Account -
flux bootstrap github \
--owner=$GITHUB_USER \
--repository=podinfo-app \
--branch=master \
--path=clusters/my-cluster
--personal
This will create the following components( 3 files) in the user directory

Check whether all the resources are created using the below command (Flux creates all the resources in a namespace - flux system)
kubectl get all -n flux-system
Link GitHub repo to the flux-system -
We plan to employ the GitOps technique by leaving the rest to Flux CD and simply committing new definitions to the GitHub repository. Updated resource definitions from the repository should be automatically retrieved by Flux CD and applied to the cluster.
We need to generate two resource definitions to employ GitOps,we can simply do by running the following two commands -
# Generate GitRepository Resource YAML
flux create source git podinfo \
--url=https://github.com/$GITHUB_USER/podinfo-app \
--branch=master \ # track master branch
--export > ./clusters/my-cluster/podinfo-source.yaml
# Generate Kustomization Resource YAML
flux create kustomization podinfo \
--target-namespace=default \ # namespace where application needs to run
--source=podinfo-app \
--prune=true \
--export > ./clusters/my-cluster/podinfo-kustomization.yaml
We use Kustomize (A customizable Kubernetes resource configuration tool, removing the need for templates like Helm)
These are YAML Created
-- ./clusters/my-cluster/podinfo-source.yaml
apiVersion: source.toolkit.fluxcd.io/v1
kind: GitRepository
metadata:
name: podinfo
namespace: flux-system
spec:
interval: 30s
ref:
branch: master
url: https://github.com/$GITHUB_USER/podinfo-ap
-- ./clusters/my-cluster/podinfo-kustomization.yaml
apiVersion: kustomize.toolkit.fluxcd.io/v1
kind: Kustomization
metadata:
name: podinfo
namespace: flux-system
spec:
interval: 5m0s
path: ./kustomize
prune: true
sourceRef:
kind: GitRepository
name: podinfo-app
targetNamespace: default
Now you can add and push the two new resource files and see Flux CD update your cluster automatically.
git add -A && git commit -m "Flux Application"
git push
Voila! Your Deployments are now GitOps’ified !!
To watch the deployments, run the below command -
flux get kustomizations --watch
Integrating FluxCD with your workflow is this simple!
FAQs
1. What is GitOps, and how does it help with Kubernetes deployments?
GitOps is a modern approach to Kubernetes management that treats Git as the single source of truth for infrastructure and application configurations. It automates deployments by continuously syncing Kubernetes clusters with the state defined in a Git repository, ensuring consistency, reliability, and simplified rollbacks.
2. How does FluxCD compare to ArgoCD?
Both FluxCD and ArgoCD are GitOps tools for Kubernetes, but they have differences:
FluxCD is pull-based, lightweight, and integrates well with Kubernetes-native tools like Kustomize and Helm.
ArgoCD offers a UI dashboard and more advanced deployment strategies, but it has a heavier footprint.
3. How does FluxCD ensure security in GitOps workflows?
FluxCD operates using pull-based workflows, ensuring that changes are securely fetched rather than pushed into the cluster. It also follows the principle of least privilege access and integrates with security tools like Open Policy Agent (OPA) and Kyverno to enforce policies and protect sensitive resources.
4. What are some best practices for implementing GitOps with FluxCD?
Maintain a clear Git branching strategy (e.g., feature branches, staging, and production).
Use Kustomize or Helm to manage Kubernetes manifests.
Implement role-based access control (RBAC) and secrets management.
Regularly monitor and audit Git commits to track changes.
Automate testing and validation of manifests before deployment.
5. Can I use FluxCD with Helm for package management?
Yes, FluxCD includes a Helm Controller that allows declarative management of Helm releases. It watches for changes in HelmRelease objects and automatically applies updates from Helm repositories, ensuring seamless application rollouts.
6. How does FluxCD handle container image updates?
FluxCD uses Image Reflection and Image Automation Controllers to detect new container image versions. It scans image repositories, updates YAML manifests with the latest images, and commits these changes back to Git, triggering automated deployments.

